Pre-requisite
- Dockers, docker network and docker compose.
- Directus Headless CMS
- Microsoft AD SSO with OpenID
Microsoft AD Setup
Create an AD application for web.
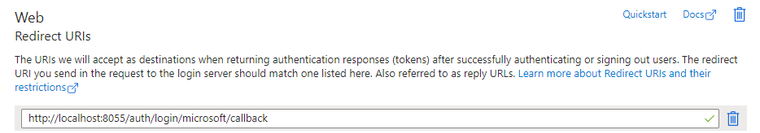
Add a Redirect URIs in AD application for login callback purpose,
<instance domain>/auth/login/microsoft/callback
(It only allowed http with localhost or https with non-localhost.)
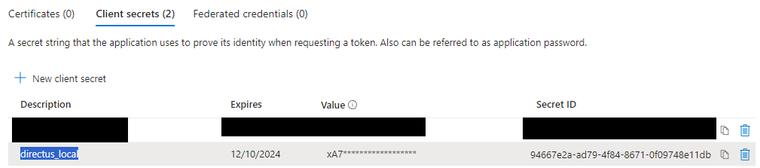
Create a Client Secrets in AD application, keep the value when secret is generated.
Specify the provider in docker-compose.yml file, under environment of directus.
AUTH_PROVIDERS: "microsoft" AUTH_MICROSOFT_DRIVER: "openid" AUTH_MICROSOFT_CLIENT_ID: <Application (client) ID> AUTH_MICROSOFT_CLIENT_SECRET: <Client Secrets generated> AUTH_MICROSOFT_ISSUER_URL: "https://login.microsoftonline.com/<Directory (tenant) ID>/v2.0/.well-known/openid-configuration" AUTH_MICROSOFT_SCOPE: <check the well-known metadata endpoint to confirm what scope is supported, usually are "openid profile email"> AUTH_MICROSOFT_IDENTIFIER_KEY: <check the well-known metadata endpoint to confirm what claim is supported, usually is "email"> AUTH_MICROSOFT_ICON: <Fontawesome icon name, e.g. microsoft> AUTH_MICROSOFT_LABEL: <Button label, it will show "Login with `label`"> AUTH_MICROSOFT_DEFAULT_ROLE_ID: <role_id - Get the role id from URL address when access the role in “Access Control” → “<Role>”>
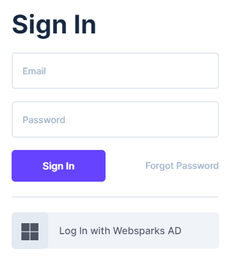
Restart docker instance, then you shall see the login button,
References
- https://github.com/khezen/compose-postgres
- https://www.sqlshack.com/getting-started-with-postgresql-on-docker/
- https://github.com/FL0R1AN84/directus-docker-compose/blob/main/docker-compose.yml
- https://github.com/directus/directus/blob/main/docker-compose.yml
- https://docs.directus.io/self-hosted/config-options.html
- https://www.docker.com/products/docker-desktop/
- https://docs.directus.io/self-hosted/sso.html
This article first appeared on Hawjeh Blog.





